The Best Certifications for 2021
As we start to heal from the bumps and bruises caused by 2020, we are now able to rise like the proverbial phoenix from the ashes with the fresh promises of 2021. As we refocus future goals and aspirations now is the perfect time to consider a career in IT. Careers in IT have proven that not only, do they promise job stability, the enormous amount of growth potential is endless. In this blog we will discuss just a fraction of the most desired IT certifications for 2021.
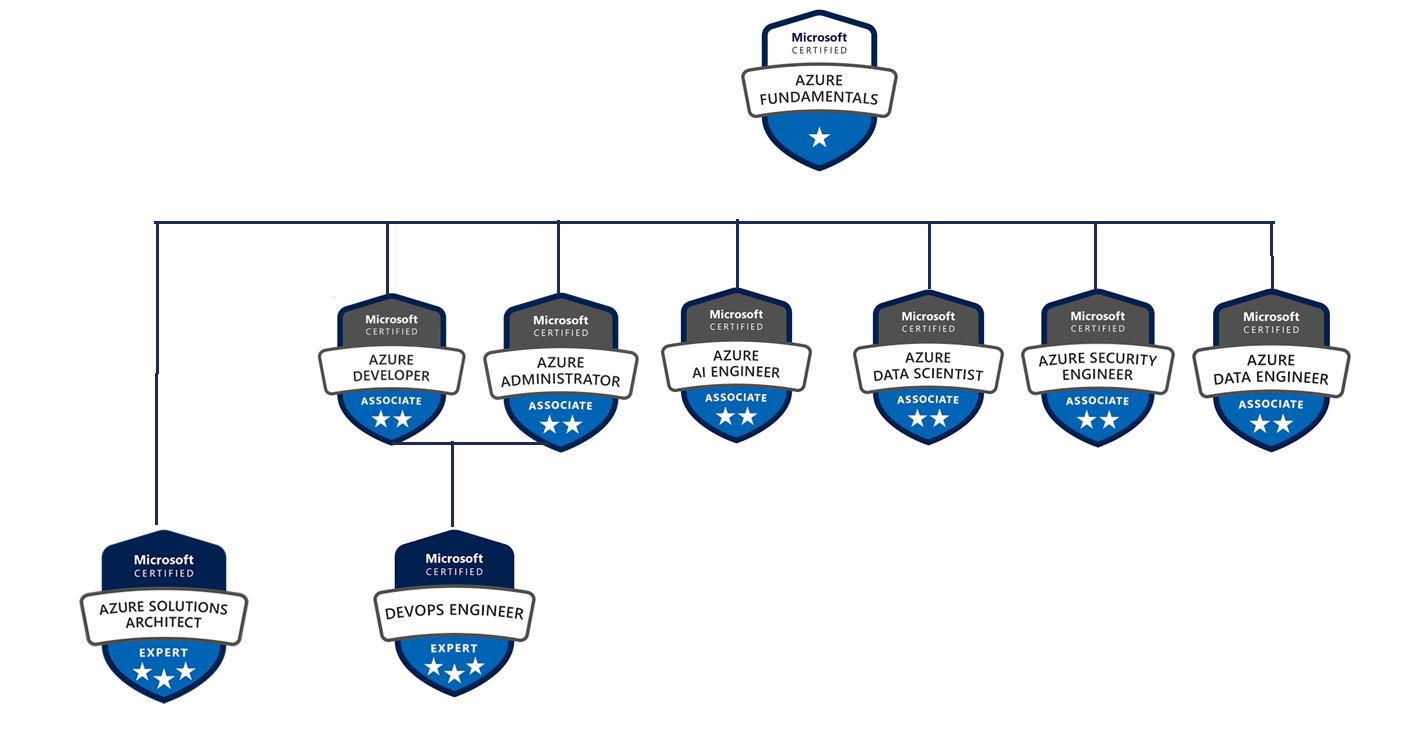
Careers in Azure
Within the last few years cloud computing has been becoming the preferred method of storage and networking for businesses worldwide. With the drastic shift from normalcy in 2020, everyone had to adjust their daily lifestyles and work environments causing the need to  incorporate cloud computing services to skyrocket. The sharp rise in demand for qualified candidates to facilitate an organization’s cloud environment put an incredible strain on businesses. From 2015 to 2020 the compound annual growth rate jumped from $70B to more than $141B, with the projected worldwide spending growing by 20% this is one of the highest growth rates anticipated for any career in 2021. Solutions Architects and DevOps Engineers are some of the most sought-after job roles to fill and typically provide higher than average salaries. The average salary for a Solutions Architect is in the $136k range whereas, the median salary for a DevOps Engineer starts around $115k. If you are considering a career in cloud computing and unsure of which direction to go the easiest way to discern the main differences between a Solutions Architect and a DevOps Engineer is this: DevOps Engineers focuses on “how things get done” whereas, Solutions Architects focus on “how things can be done.” DevOps Engineers are responsible for supporting the infrastructure they develop while also being the first line of defense in protecting the cloud against malicious attacks. Solutions Architects focus on the applications or services within an organization’s infrastructure. They are responsible for creating a comprehensive architecture for software solutions and strategic direction throughout development. Each of these certifications provide tremendous growth and income potential while providing massive job stability.
incorporate cloud computing services to skyrocket. The sharp rise in demand for qualified candidates to facilitate an organization’s cloud environment put an incredible strain on businesses. From 2015 to 2020 the compound annual growth rate jumped from $70B to more than $141B, with the projected worldwide spending growing by 20% this is one of the highest growth rates anticipated for any career in 2021. Solutions Architects and DevOps Engineers are some of the most sought-after job roles to fill and typically provide higher than average salaries. The average salary for a Solutions Architect is in the $136k range whereas, the median salary for a DevOps Engineer starts around $115k. If you are considering a career in cloud computing and unsure of which direction to go the easiest way to discern the main differences between a Solutions Architect and a DevOps Engineer is this: DevOps Engineers focuses on “how things get done” whereas, Solutions Architects focus on “how things can be done.” DevOps Engineers are responsible for supporting the infrastructure they develop while also being the first line of defense in protecting the cloud against malicious attacks. Solutions Architects focus on the applications or services within an organization’s infrastructure. They are responsible for creating a comprehensive architecture for software solutions and strategic direction throughout development. Each of these certifications provide tremendous growth and income potential while providing massive job stability.
Careers in Cybersecurity
With the ever-growing dependency on technology it is no surprise people have created ways of maliciously obtaining private data/personal information, especially with the birth of the cloud. As businesses integrate more and more data to the cloud, the need to circumvent any potential cybersecurity risk by equipping their team with qualified cybersecurity experts increases substantially. In 2020 alone, $123B was spent on cybersecurity defenses with that number projected to grow another 33%. Businesses understand the limitless liability should a data breach or personal information be jeopardized and have invested accordingly. Two of the most in-demand/higher paying certifications include Information Systems Security Manager (CISSM) and Certified Information Systems Security Professionals (CISSP). Information Systems Security Manager (CISSM) and Certified Information Systems Security Professionals (CISSP) are similar but the main difference is that CISSM certification is solely management-focused, whereas the CISSP certification is both technical and managerial. The Certified Information Systems Security Professionals (CISSP) certification was developed by the International Information Systems Security Certification Consortium, also referred to as (ISC)2 This is one of the world’s most valued certifications. Obtaining a CISSP certification validates expertise in designing, architecture, controls, and the management of secure business environments. An average starting salary for Certified Information Systems Security Professionals (CISSP) is around $120k with that figure growing substantially yearly. The Information Systems Security Manager (CISSM) certification is designed for candidates that oversee, design or assess an organization’s security systems. They also provide direction when analyzing and evaluating networks and security vulnerabilities. An average salary for a candidate that holds an Information Systems Security Manager (CISSM) certification is around $130k annually. With estimated global losses from cybercrime projected to hit under $1 trillion in 2020 alone it is no wonder why businesses have increased their cybersecurity budgets by 60%. As cybercrime continues to intensify there is enormous (job) security in cybersecurity roles (pun kind of intended…)
Careers in Project Management
With the diversification of technology options for organizations to utilize it is no wonder that Project Management certifications are on the rise. Project managers are a vital necessity for organizations to remain on task by successfully initiating, designing, planning, controlling, executing, monitoring, and closing projects. As of 2020 15 million project management jobs were created with that figure steadily increasing. The Certified Associate in Project Management (CAPM) and Project Management Professional (PMP) are both specialized certifications that are in high demand. The Certified Associate in Project Management (CAPM) is an entry-level  certification designed for those with less project management experience. This certification is the precursor to the Project Management Professional (PMP) certification and demonstrates the understanding of the fundamental knowledge and processes for effective project management. The average salary for a candidate with this certificate is around $73k with substantial room for growth. The Project Management Professional (PMP) is the “gold standard” of project management certifications. Obtaining the Project Management Professional (PMP) certificate validates your competency to perform all requirements of the project manager role including the leading and direction of projects and teams. Adding this certification to your arsenal increases your salary average to $113k. The demand for project managers is growing faster than the qualified talent pool allows. It is anticipated that by 2027, employers will require around 88 million new roles within project management. Needless to say, project managers aren’t going anywhere anytime soon.
certification designed for those with less project management experience. This certification is the precursor to the Project Management Professional (PMP) certification and demonstrates the understanding of the fundamental knowledge and processes for effective project management. The average salary for a candidate with this certificate is around $73k with substantial room for growth. The Project Management Professional (PMP) is the “gold standard” of project management certifications. Obtaining the Project Management Professional (PMP) certificate validates your competency to perform all requirements of the project manager role including the leading and direction of projects and teams. Adding this certification to your arsenal increases your salary average to $113k. The demand for project managers is growing faster than the qualified talent pool allows. It is anticipated that by 2027, employers will require around 88 million new roles within project management. Needless to say, project managers aren’t going anywhere anytime soon.
Make 2021 Your Year
As a society that is increasingly becoming more and more dependent on all forms of technology, organizations are scrambling to find qualified candidates to fill these dynamic roles. Whether you want a career in the cloud, cybersecurity, or project management, the considerable growth rate in each role is beyond the average rates for other occupations. Now is the time to invest in your future and become certified today. Learn more here.










 through new insights and capturing new advantages through cloud-based advances. Quickly catching up to its competitors at an astonishing rate it has been reported that the cloud service provider has a YOY (year over year) growth rate of 154% (as of 2020) and the total number of companies adapting and utilizing Microsoft Azure has grown to nearly 400,000. With many more businesses shifting to cloud-based operations it is no wonder why the U.S. Bureau of Labor Statistics currently projects a higher than average growth rate of 10% within the Azure Administrator field. Companies are constantly looking for employees with the right skillset and it has been shown that candidates that have the Azure Administrator certification not only improve their salary, it also allows them the opportunity to secure their current position (job security) or lock in that promotion. With the current median pay looming around $84,000/year it is no wonder why this certification is so alluring to so many.
through new insights and capturing new advantages through cloud-based advances. Quickly catching up to its competitors at an astonishing rate it has been reported that the cloud service provider has a YOY (year over year) growth rate of 154% (as of 2020) and the total number of companies adapting and utilizing Microsoft Azure has grown to nearly 400,000. With many more businesses shifting to cloud-based operations it is no wonder why the U.S. Bureau of Labor Statistics currently projects a higher than average growth rate of 10% within the Azure Administrator field. Companies are constantly looking for employees with the right skillset and it has been shown that candidates that have the Azure Administrator certification not only improve their salary, it also allows them the opportunity to secure their current position (job security) or lock in that promotion. With the current median pay looming around $84,000/year it is no wonder why this certification is so alluring to so many. CompTIA A+ first launched in 1993, and since 2001 has been refreshed every three years to ensure the topics covered keep pace with what’s happening in IT. Employers, subject-matter experts and IT pros working in the field guide us in what they look for in help desk technicians, technical support specialists and other jobs related to CompTIA A+ to make sure we’re covering the skills that are needed in today’s world. With the launch of the new CompTIA A+ came many questions, so we’ve set out to answer them here. Keep reading to learn more about the
CompTIA A+ first launched in 1993, and since 2001 has been refreshed every three years to ensure the topics covered keep pace with what’s happening in IT. Employers, subject-matter experts and IT pros working in the field guide us in what they look for in help desk technicians, technical support specialists and other jobs related to CompTIA A+ to make sure we’re covering the skills that are needed in today’s world. With the launch of the new CompTIA A+ came many questions, so we’ve set out to answer them here. Keep reading to learn more about the 